Jan 18, 2026
Google's Agent2Agent Protocol Explained for Enterprise AI Teams


Jackson Wells
Integrated Marketing
Jackson Wells
Integrated Marketing


Your customer service agent needs to check inventory, your inventory agent must coordinate with suppliers, and those supplier agents operate on completely different platforms. Right now, each integration requires custom code, proprietary APIs, and weeks of engineering time.
Google's Agent2Agent (A2A) protocol addresses this fragmentation with a standardized communication layer that enables AI agents from different vendors and frameworks to discover, authenticate, and collaborate seamlessly.
TLDR:
A2A is an open-source protocol for secure agent-to-agent communication across platforms
Uses standard web technologies (JSON-RPC 2.0, HTTP/HTTPS, SSE) for straightforward integration
Different from MCP: A2A handles agent coordination; MCP connects agents to tools
Addresses vendor lock-in identified as a critical AI blind spot
Early adoption phase: Microsoft integrated; limited production deployments as of early 2025
Linux Foundation governance provides vendor-neutral community development
What Is Google's Agent2Agent Protocol?
Google's Agent2Agent (A2A) protocol is an open-source communication standard that enables autonomous AI agents to discover, authenticate, and interact with each other regardless of their underlying implementation or hosting platform.
Released in April 2025 under Apache-2.0 licensing and now governed by the Linux Foundation, A2A provides the interoperability layer that multi-agent systems require to operate across organizational and vendor boundaries.
A2A addresses a specific technical challenge: your agents built with different frameworks, deployed on different clouds, and operated by different organizations need to collaborate on complex workflows without requiring custom integration code for each connection.
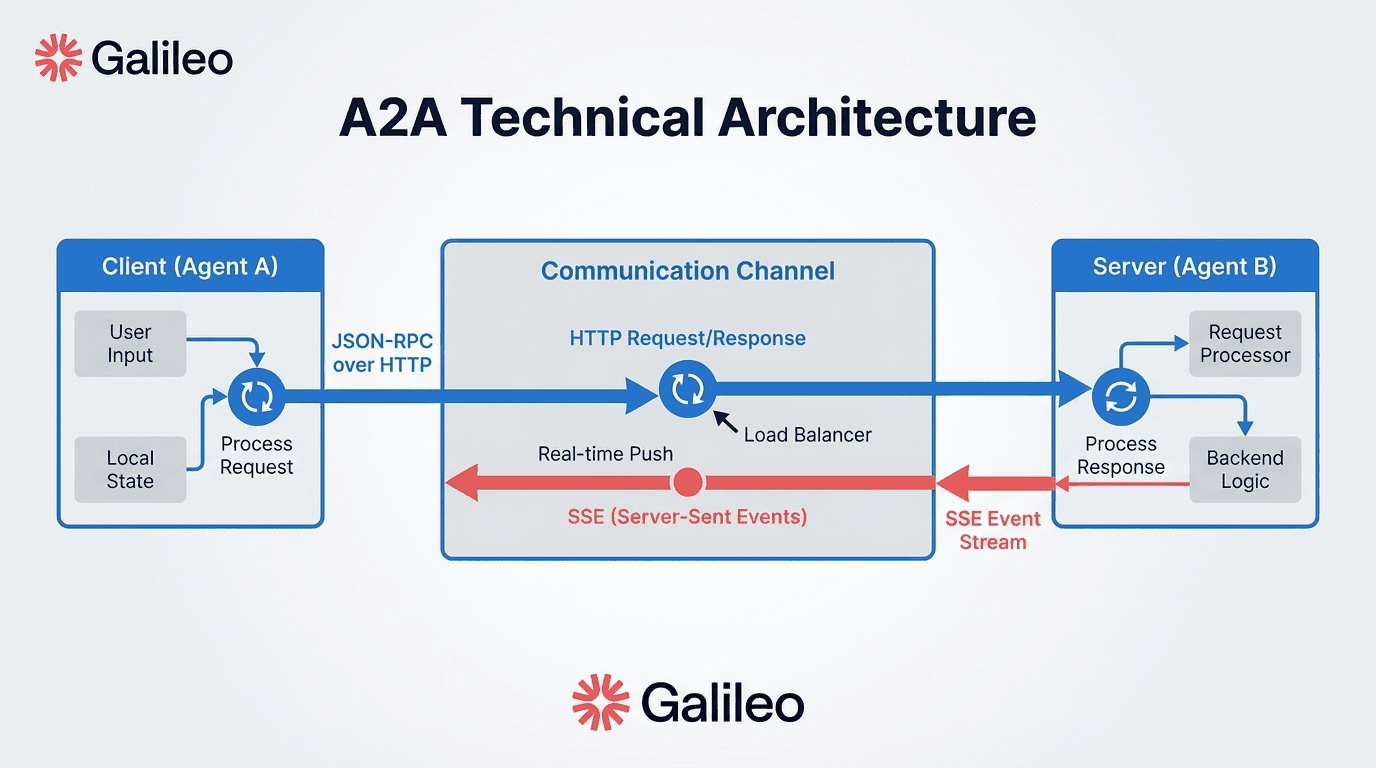
A2A achieves this through standardized discovery mechanisms using Agent Cards, structured task management with defined lifecycle states, and enterprise-grade security including OAuth 2.0, API Keys, and mTLS support, all built on familiar web technologies (HTTP/HTTPS, JSON-RPC 2.0, Server-Sent Events) that your teams already understand.
Why enterprises need standardized agent interoperability

You face converging pressures that standardized protocols directly address. Vendor lock-in risks limit technical agility and weaken negotiating leverage. Integration complexity consumes 20-40% of engineering resources. Governance gaps in autonomous systems require comprehensive frameworks.
Industry analysts identify ecosystem lock-in as critical generative AI blind spots that CIOs must address to avoid project failures. While choosing a single vendor accelerates initial deployment, this creates dependency risks that constrain your technical options on pricing and service levels.
Organizations spend 20-40% of development time on integration maintenance. Without standardized protocols, integration complexity grows quadratically while engineering capacity remains linear.
Multi-agent systems increase organizational risk through multiple interacting autonomous agents, each making decisions that impact business outcomes and regulatory compliance. Comprehensive governance requirements include:
Identity and access management for agents operating across systems
Third-party risk management for agent interactions with external systems
Continuous monitoring with audit trails for accountability
Risk assessment frameworks adapted for autonomous decision-making
Without standardized protocols, implementing consistent AI guardrails across heterogeneous agent systems becomes exponentially complex.
Standardized agent communication protocols enable comprehensive observability across multi-agent workflows by providing unified visibility into agent interactions regardless of which vendor built each agent. When agents communicate through standardized protocols like A2A, monitoring becomes possible at the protocol level: tracking decision-making across workflows, identifying failure patterns, and maintaining audit trails required for compliance.
Core technical architecture and components
Understanding A2A's architecture reveals how it reduces integration friction while maintaining enterprise security standards. The protocol builds on technologies your teams already understand rather than introducing proprietary systems, making adoption more straightforward than custom agent-to-agent solutions that require specialized knowledge.
A2A builds on standards your teams already understand rather than introducing proprietary protocols. The architecture uses JSON-RPC 2.0 over HTTP/HTTPS for request-response patterns and Server-Sent Events (SSE) for real-time streaming, providing language-agnostic integration with standard web security through TLS.
Discovery mechanisms enable dynamic agent coordination
Agent Cards are JSON metadata files that function as machine-readable capability advertisements. Each agent hosts its Agent Card at the standardized well-known URI path /.well-known/agent.json, following RFC 8615 conventions. The card declares service endpoints, supported authentication schemes, skill descriptions with input/output modes, and specific task capabilities.
This standardized discovery mechanism allows any A2A client to programmatically discover what a remote agent can do without requiring vendor-specific knowledge. The cards support OAuth 2.0, API keys, OpenID Connect, and bearer tokens, giving you flexibility to match your organization's security policies.
Structured lifecycle tracking manages distributed workflows
A2A's task management system is specifically designed to handle long-running operations with defined lifecycle states. The protocol enables agents to track tasks through pending, in-progress, completed, and failed states, with Server-Sent Events (SSE) streaming real-time progress updates. This approach reduces network overhead while maintaining visibility into distributed workflows.
The protocol structures agent communication through Message Objects that support multiple content modalities. Message Parts can contain text, images, structured data, or other formats, allowing agents to exchange whatever data types their workflows require.
Artifact handling provides typed data exchange between agents. When one agent produces outputs that another agent needs (documents, images, executable code, or structured datasets), Artifacts provide the container format with metadata about content type, encoding, and semantics.
How A2A enables cross-vendor communication
The protocol achieves vendor-agnostic interoperability through five foundational design principles: embracing agentic capabilities for autonomous decision-making, building on existing standards rather than proprietary protocols, implementing security by default with enterprise-grade authentication, supporting long-running task lifecycles, and maintaining modality agnosticism for diverse content types.
Web standards foundation accelerates integration
A2A's foundation on established web standards (HTTP(S), JSON-RPC 2.0, and Server-Sent Events) directly reduces integration complexity that typically consumes 20-40% of development time in AI agent deployments.
By leveraging protocols that engineering teams already understand, the protocol reduces switching costs and enables language-agnostic integration through standardized request/response patterns.
The client-server architecture enables agents built with different frameworks to communicate without requiring knowledge of internal implementations. Microsoft has demonstrated this interoperability by integrating Semantic Kernel agents with the A2A protocol, enabling heterogeneous agent systems to coordinate with agents from different vendors and platforms operating alongside each other.
Enterprise security requires multiple authentication layers
Enterprise-grade security becomes essential when agents operated by different organizations communicate across trust boundaries. A2A incorporates multiple authentication mechanisms aligned with OpenAPI standards:
OAuth 2.0 for delegated authorization
Mutual TLS certificates for strong mutual authentication
JWT (JSON Web Tokens) for stateless authentication
API keys for simpler authentication scenarios
OpenID Connect for identity verification
Independent security analysis validates the protocol's Agent Card management security, authentication flows, and authorization enforcement mechanisms, though you should be aware of identified limitations in sensitive data handling that may require additional security enhancements beyond the base specification.
A2A protocol and Anthropic's MCP serve different purposes
Choosing the right protocol, or combination, depends on understanding which communication problems you're actually solving. A2A and MCP address fundamentally different architectural challenges in your agent infrastructure, and confusion between them leads to mismatched implementations.
Architecture models determine communication patterns
A2A implements a client-server model supporting Agent Cards for discovery, Task Management for structured lifecycles, Message-Based Collaboration for bidirectional agent communication, and Artifact Handling for typed data exchange. The architecture supports many-to-many agent relationships enabling mesh topologies where agents collaborate as peers.
MCP defines a client-server model where an AI application (MCP Host) maintains connections to tool servers providing context and capabilities. The key distinction: A2A enables peer-to-peer agent collaboration with bidirectional communication, while MCP implements a hub-and-spoke model where your AI application serves as the central orchestrator accessing tool servers and context providers.
Choosing between agent coordination and tool integration
Consider A2A when multiple autonomous agents need to collaborate across organizational boundaries. Picture this: your hiring pipeline with separate agents for screening, scheduling, and background checks requires agent-to-agent coordination through task delegation. Supply chain workflows where your agents must coordinate with external partner agents demand cross-organizational communication.
Choose MCP when one agent needs standardized access to multiple tools, data sources, or business systems. Suppose your customer support agent needs both capabilities. It uses MCP to access your knowledge base, ticket system, and customer database, standardizing how the agent connects to these tools. But when complex cases require escalation, your support agent uses A2A to coordinate with specialized agents handling refunds, technical issues, or billing disputes.
Implementation guidance for engineering teams
Your teams face several critical decisions when adopting A2A for production agent systems.
SDKs reduce integration risk and accelerate deployment
Begin with the official Python SDK rather than implementing the protocol from scratch. This decision cuts weeks of integration time while reducing the risk of protocol implementation errors that lead to production failures.
The SDK handles JSON-RPC formatting, HTTP transport management, and SSE streaming, allowing your developers to focus on agent logic rather than protocol plumbing. For teams building on Google Cloud, the Agent Development Kit provides higher-level abstractions managing connections and authentication automatically.
Study reference implementations before custom development. These samples demonstrate agent creation, task handling, client-server interactions, and complete workflow patterns, providing validated patterns your teams can adapt.
Orchestration patterns simplify complex workflows
Implement orchestrator agent patterns for complex workflows requiring coordination across multiple specialized agents. Orchestrator patterns reduce debugging complexity that typically consumes 20-40% of engineering time in distributed agent systems.
The orchestrator handles task decomposition into subtasks, delegates work to appropriate agents based on their declared capabilities in Agent Cards, manages state across the distributed workflow, and aggregates results from multiple agents.
When designing multi-agent systems with long-running tasks, implement proper error recovery and monitoring mechanisms to track task progress and agent interactions. A2A's task management system uses defined lifecycle states (pending, in-progress, completed, failed) to support extended workflows across distributed agents.
Production readiness and current adoption
As of early 2025, A2A protocol remains in early adoption phase with limited production deployment evidence. Understanding the maturity landscape helps your teams make informed architectural decisions.
Microsoft provides substantiated production-oriented implementation
Microsoft provides the most substantiated production-oriented implementation through Semantic Kernel integration. Microsoft's engineering team documented architecture details, provided code examples, and demonstrated multi-agent coordination through standardized communication. The travel planning reference shows a TravelManager agent coordinating with specialized sub-agents for flights, hotels, and activities.
Google announced partnerships with over 50 technology partners including Atlassian, Box, Intuit, MongoDB, PayPal, Salesforce, SAP, and ServiceNow, plus consulting firms like Accenture, BCG, Deloitte, and McKinsey. These partnerships represent commitments to support the protocol rather than verified production implementations.
Plan proof-of-concept validation before architectural commitments
Your teams should plan proof-of-concept validation before major architectural commitments. Test the protocol with representative workflows, validate security implementations meet your requirements, benchmark performance under realistic loads, and evaluate SDK maturity for your technology stack.
Think about phased adoption starting with non-critical workflows to gain operational experience, expanding to more critical systems as the ecosystem matures. Implement abstraction layers that accommodate protocol evolution or alternative standards.
Linux Foundation governance reduces long-term vendor risk
The transfer to Linux Foundation governance represents a fundamental shift from Google proprietary control to vendor-neutral community development under an open governance model. This governance structure reduces long-term vendor lock-in risk compared to single-vendor controlled specifications.
Active standards development continues across IEEE, W3C, and IETF working groups addressing agent communication in various contexts. The realistic future state involves multiple coexisting protocols rather than winner-takes-all outcomes. Design your architectures with abstraction layers accommodating protocol diversity as the ecosystem matures.
Agent interoperability shapes the future of enterprise AI
Standardized agent communication protocols transition from nice-to-have abstractions to strategic infrastructure requirements. Industry analysts project that by the end of 2026, 40% of enterprise applications will include task-specific AI agents, while simultaneously identifying ecosystem lock-in and interoperability as critical AI blind spots.
This convergence creates a strategic imperative for standardized protocols that prevent vendor lock-in while enabling sophisticated multi-agent workflows.
Galileo's platform provides the monitoring infrastructure that standardized protocols enable:
Agent Graph visualization: Map agent-to-agent communication flows across your entire ecosystem, identifying bottlenecks and failure patterns in multi-agent workflows regardless of which frameworks power each agent
Agent Protect with real-time guardrails: Block unsafe agent outputs before they reach production, enforcing compliance policies across heterogeneous agent systems communicating through A2A protocol
Insights Engine for multi-agent debugging: Trace decision paths through distributed workflows, pinpointing where agent handoffs fail and why task delegation breaks across vendor boundaries
Luna-2 evaluation models: Automatically assess agent output quality, hallucination rates, and task completion accuracy across agents using A2A for coordination
Protocol-agnostic monitoring: Track agent performance whether they communicate via A2A, MCP, or proprietary protocols—unified observability across your entire agent infrastructure
See how Galileo provides unified observability across multi-agent systems using A2A, MCP, and proprietary protocols—request a demo to visualize your agent ecosystem.
Frequently Asked Questions
What is the main difference between A2A and MCP protocols?
A2A enables peer-to-peer agent-to-agent coordination for multi-agent workflows through a client-server architecture where agents act as both clients and servers, while MCP implements a hub-and-spoke model connecting a single agent to multiple tools and data sources. A2A solves the horizontal problem of enabling autonomous agents to collaborate across different platforms and organizational boundaries; MCP solves the vertical problem of augmenting a single agent's capabilities through standardized tool integration. The two protocols are complementary, with MCP handling model context and tools while A2A handles agent-to-agent orchestration.
How do I implement A2A protocol authentication for production agents?
Start with the official Python SDK or Agent Development Kit (ADK), which handles authentication flows automatically. For machine-to-machine communication, implement OAuth 2.0 client credentials flow and mutual TLS for high-security environments. Secure all authentication tokens using dedicated secret management systems and rotate credentials according to organizational policies. Validate authorization at every agent interaction point and design Agent Cards with minimal necessary permissions.
Is A2A protocol ready for production enterprise deployments in 2026?
A2A launched in April 2025, making it relatively new with limited production evidence. Microsoft's Semantic Kernel integration demonstrates technical viability, with a documented multi-agent travel planning use case on Azure App Service. However, most announced partnerships lack verified production deployments. Plan proof-of-concept validation before major commitments, start with non-critical workflows, and maintain architectural flexibility as the ecosystem matures.
How does A2A protocol handle long-running agent workflows?
A2A implements structured task lifecycles with defined states (pending, in-progress, completed, failed) and uses Server-Sent Events for real-time progress streaming. Agents submit tasks and receive task identifiers for tracking, subscribe to status updates rather than polling, and retrieve results when workflows complete asynchronously, supporting operations spanning hours or days.
Can Galileo monitor agents using the A2A protocol?
Standardized protocols like A2A enable unified visibility across multi-agent systems through defined communication standards. The protocol's architecture supports tracing agent decision paths through structured message logging, detecting failure patterns through standardized error handling and task lifecycle states, enforcing security guardrails through built-in authentication and authorization mechanisms, and maintaining audit trails through documented task states and transaction logs. This standardized approach enables observability across agents regardless of which vendor built each agent.
Your customer service agent needs to check inventory, your inventory agent must coordinate with suppliers, and those supplier agents operate on completely different platforms. Right now, each integration requires custom code, proprietary APIs, and weeks of engineering time.
Google's Agent2Agent (A2A) protocol addresses this fragmentation with a standardized communication layer that enables AI agents from different vendors and frameworks to discover, authenticate, and collaborate seamlessly.
TLDR:
A2A is an open-source protocol for secure agent-to-agent communication across platforms
Uses standard web technologies (JSON-RPC 2.0, HTTP/HTTPS, SSE) for straightforward integration
Different from MCP: A2A handles agent coordination; MCP connects agents to tools
Addresses vendor lock-in identified as a critical AI blind spot
Early adoption phase: Microsoft integrated; limited production deployments as of early 2025
Linux Foundation governance provides vendor-neutral community development
What Is Google's Agent2Agent Protocol?

Google's Agent2Agent (A2A) protocol is an open-source communication standard that enables autonomous AI agents to discover, authenticate, and interact with each other regardless of their underlying implementation or hosting platform.
Released in April 2025 under Apache-2.0 licensing and now governed by the Linux Foundation, A2A provides the interoperability layer that multi-agent systems require to operate across organizational and vendor boundaries.
A2A addresses a specific technical challenge: your agents built with different frameworks, deployed on different clouds, and operated by different organizations need to collaborate on complex workflows without requiring custom integration code for each connection.
A2A achieves this through standardized discovery mechanisms using Agent Cards, structured task management with defined lifecycle states, and enterprise-grade security including OAuth 2.0, API Keys, and mTLS support, all built on familiar web technologies (HTTP/HTTPS, JSON-RPC 2.0, Server-Sent Events) that your teams already understand.
Why enterprises need standardized agent interoperability

You face converging pressures that standardized protocols directly address. Vendor lock-in risks limit technical agility and weaken negotiating leverage. Integration complexity consumes 20-40% of engineering resources. Governance gaps in autonomous systems require comprehensive frameworks.
Industry analysts identify ecosystem lock-in as critical generative AI blind spots that CIOs must address to avoid project failures. While choosing a single vendor accelerates initial deployment, this creates dependency risks that constrain your technical options on pricing and service levels.
Organizations spend 20-40% of development time on integration maintenance. Without standardized protocols, integration complexity grows quadratically while engineering capacity remains linear.
Multi-agent systems increase organizational risk through multiple interacting autonomous agents, each making decisions that impact business outcomes and regulatory compliance. Comprehensive governance requirements include:
Identity and access management for agents operating across systems
Third-party risk management for agent interactions with external systems
Continuous monitoring with audit trails for accountability
Risk assessment frameworks adapted for autonomous decision-making
Without standardized protocols, implementing consistent AI guardrails across heterogeneous agent systems becomes exponentially complex.
Standardized agent communication protocols enable comprehensive observability across multi-agent workflows by providing unified visibility into agent interactions regardless of which vendor built each agent. When agents communicate through standardized protocols like A2A, monitoring becomes possible at the protocol level: tracking decision-making across workflows, identifying failure patterns, and maintaining audit trails required for compliance.
Core technical architecture and components
Understanding A2A's architecture reveals how it reduces integration friction while maintaining enterprise security standards. The protocol builds on technologies your teams already understand rather than introducing proprietary systems, making adoption more straightforward than custom agent-to-agent solutions that require specialized knowledge.
A2A builds on standards your teams already understand rather than introducing proprietary protocols. The architecture uses JSON-RPC 2.0 over HTTP/HTTPS for request-response patterns and Server-Sent Events (SSE) for real-time streaming, providing language-agnostic integration with standard web security through TLS.
Discovery mechanisms enable dynamic agent coordination
Agent Cards are JSON metadata files that function as machine-readable capability advertisements. Each agent hosts its Agent Card at the standardized well-known URI path /.well-known/agent.json, following RFC 8615 conventions. The card declares service endpoints, supported authentication schemes, skill descriptions with input/output modes, and specific task capabilities.
This standardized discovery mechanism allows any A2A client to programmatically discover what a remote agent can do without requiring vendor-specific knowledge. The cards support OAuth 2.0, API keys, OpenID Connect, and bearer tokens, giving you flexibility to match your organization's security policies.
Structured lifecycle tracking manages distributed workflows
A2A's task management system is specifically designed to handle long-running operations with defined lifecycle states. The protocol enables agents to track tasks through pending, in-progress, completed, and failed states, with Server-Sent Events (SSE) streaming real-time progress updates. This approach reduces network overhead while maintaining visibility into distributed workflows.
The protocol structures agent communication through Message Objects that support multiple content modalities. Message Parts can contain text, images, structured data, or other formats, allowing agents to exchange whatever data types their workflows require.
Artifact handling provides typed data exchange between agents. When one agent produces outputs that another agent needs (documents, images, executable code, or structured datasets), Artifacts provide the container format with metadata about content type, encoding, and semantics.
How A2A enables cross-vendor communication
The protocol achieves vendor-agnostic interoperability through five foundational design principles: embracing agentic capabilities for autonomous decision-making, building on existing standards rather than proprietary protocols, implementing security by default with enterprise-grade authentication, supporting long-running task lifecycles, and maintaining modality agnosticism for diverse content types.
Web standards foundation accelerates integration
A2A's foundation on established web standards (HTTP(S), JSON-RPC 2.0, and Server-Sent Events) directly reduces integration complexity that typically consumes 20-40% of development time in AI agent deployments.
By leveraging protocols that engineering teams already understand, the protocol reduces switching costs and enables language-agnostic integration through standardized request/response patterns.
The client-server architecture enables agents built with different frameworks to communicate without requiring knowledge of internal implementations. Microsoft has demonstrated this interoperability by integrating Semantic Kernel agents with the A2A protocol, enabling heterogeneous agent systems to coordinate with agents from different vendors and platforms operating alongside each other.
Enterprise security requires multiple authentication layers
Enterprise-grade security becomes essential when agents operated by different organizations communicate across trust boundaries. A2A incorporates multiple authentication mechanisms aligned with OpenAPI standards:
OAuth 2.0 for delegated authorization
Mutual TLS certificates for strong mutual authentication
JWT (JSON Web Tokens) for stateless authentication
API keys for simpler authentication scenarios
OpenID Connect for identity verification
Independent security analysis validates the protocol's Agent Card management security, authentication flows, and authorization enforcement mechanisms, though you should be aware of identified limitations in sensitive data handling that may require additional security enhancements beyond the base specification.
A2A protocol and Anthropic's MCP serve different purposes
Choosing the right protocol, or combination, depends on understanding which communication problems you're actually solving. A2A and MCP address fundamentally different architectural challenges in your agent infrastructure, and confusion between them leads to mismatched implementations.
Architecture models determine communication patterns
A2A implements a client-server model supporting Agent Cards for discovery, Task Management for structured lifecycles, Message-Based Collaboration for bidirectional agent communication, and Artifact Handling for typed data exchange. The architecture supports many-to-many agent relationships enabling mesh topologies where agents collaborate as peers.
MCP defines a client-server model where an AI application (MCP Host) maintains connections to tool servers providing context and capabilities. The key distinction: A2A enables peer-to-peer agent collaboration with bidirectional communication, while MCP implements a hub-and-spoke model where your AI application serves as the central orchestrator accessing tool servers and context providers.
Choosing between agent coordination and tool integration
Consider A2A when multiple autonomous agents need to collaborate across organizational boundaries. Picture this: your hiring pipeline with separate agents for screening, scheduling, and background checks requires agent-to-agent coordination through task delegation. Supply chain workflows where your agents must coordinate with external partner agents demand cross-organizational communication.
Choose MCP when one agent needs standardized access to multiple tools, data sources, or business systems. Suppose your customer support agent needs both capabilities. It uses MCP to access your knowledge base, ticket system, and customer database, standardizing how the agent connects to these tools. But when complex cases require escalation, your support agent uses A2A to coordinate with specialized agents handling refunds, technical issues, or billing disputes.
Implementation guidance for engineering teams
Your teams face several critical decisions when adopting A2A for production agent systems.
SDKs reduce integration risk and accelerate deployment
Begin with the official Python SDK rather than implementing the protocol from scratch. This decision cuts weeks of integration time while reducing the risk of protocol implementation errors that lead to production failures.
The SDK handles JSON-RPC formatting, HTTP transport management, and SSE streaming, allowing your developers to focus on agent logic rather than protocol plumbing. For teams building on Google Cloud, the Agent Development Kit provides higher-level abstractions managing connections and authentication automatically.
Study reference implementations before custom development. These samples demonstrate agent creation, task handling, client-server interactions, and complete workflow patterns, providing validated patterns your teams can adapt.
Orchestration patterns simplify complex workflows
Implement orchestrator agent patterns for complex workflows requiring coordination across multiple specialized agents. Orchestrator patterns reduce debugging complexity that typically consumes 20-40% of engineering time in distributed agent systems.
The orchestrator handles task decomposition into subtasks, delegates work to appropriate agents based on their declared capabilities in Agent Cards, manages state across the distributed workflow, and aggregates results from multiple agents.
When designing multi-agent systems with long-running tasks, implement proper error recovery and monitoring mechanisms to track task progress and agent interactions. A2A's task management system uses defined lifecycle states (pending, in-progress, completed, failed) to support extended workflows across distributed agents.
Production readiness and current adoption
As of early 2025, A2A protocol remains in early adoption phase with limited production deployment evidence. Understanding the maturity landscape helps your teams make informed architectural decisions.
Microsoft provides substantiated production-oriented implementation
Microsoft provides the most substantiated production-oriented implementation through Semantic Kernel integration. Microsoft's engineering team documented architecture details, provided code examples, and demonstrated multi-agent coordination through standardized communication. The travel planning reference shows a TravelManager agent coordinating with specialized sub-agents for flights, hotels, and activities.
Google announced partnerships with over 50 technology partners including Atlassian, Box, Intuit, MongoDB, PayPal, Salesforce, SAP, and ServiceNow, plus consulting firms like Accenture, BCG, Deloitte, and McKinsey. These partnerships represent commitments to support the protocol rather than verified production implementations.
Plan proof-of-concept validation before architectural commitments
Your teams should plan proof-of-concept validation before major architectural commitments. Test the protocol with representative workflows, validate security implementations meet your requirements, benchmark performance under realistic loads, and evaluate SDK maturity for your technology stack.
Think about phased adoption starting with non-critical workflows to gain operational experience, expanding to more critical systems as the ecosystem matures. Implement abstraction layers that accommodate protocol evolution or alternative standards.
Linux Foundation governance reduces long-term vendor risk
The transfer to Linux Foundation governance represents a fundamental shift from Google proprietary control to vendor-neutral community development under an open governance model. This governance structure reduces long-term vendor lock-in risk compared to single-vendor controlled specifications.
Active standards development continues across IEEE, W3C, and IETF working groups addressing agent communication in various contexts. The realistic future state involves multiple coexisting protocols rather than winner-takes-all outcomes. Design your architectures with abstraction layers accommodating protocol diversity as the ecosystem matures.
Agent interoperability shapes the future of enterprise AI
Standardized agent communication protocols transition from nice-to-have abstractions to strategic infrastructure requirements. Industry analysts project that by the end of 2026, 40% of enterprise applications will include task-specific AI agents, while simultaneously identifying ecosystem lock-in and interoperability as critical AI blind spots.
This convergence creates a strategic imperative for standardized protocols that prevent vendor lock-in while enabling sophisticated multi-agent workflows.
Galileo's platform provides the monitoring infrastructure that standardized protocols enable:
Agent Graph visualization: Map agent-to-agent communication flows across your entire ecosystem, identifying bottlenecks and failure patterns in multi-agent workflows regardless of which frameworks power each agent
Agent Protect with real-time guardrails: Block unsafe agent outputs before they reach production, enforcing compliance policies across heterogeneous agent systems communicating through A2A protocol
Insights Engine for multi-agent debugging: Trace decision paths through distributed workflows, pinpointing where agent handoffs fail and why task delegation breaks across vendor boundaries
Luna-2 evaluation models: Automatically assess agent output quality, hallucination rates, and task completion accuracy across agents using A2A for coordination
Protocol-agnostic monitoring: Track agent performance whether they communicate via A2A, MCP, or proprietary protocols—unified observability across your entire agent infrastructure
See how Galileo provides unified observability across multi-agent systems using A2A, MCP, and proprietary protocols—request a demo to visualize your agent ecosystem.
Frequently Asked Questions
What is the main difference between A2A and MCP protocols?
A2A enables peer-to-peer agent-to-agent coordination for multi-agent workflows through a client-server architecture where agents act as both clients and servers, while MCP implements a hub-and-spoke model connecting a single agent to multiple tools and data sources. A2A solves the horizontal problem of enabling autonomous agents to collaborate across different platforms and organizational boundaries; MCP solves the vertical problem of augmenting a single agent's capabilities through standardized tool integration. The two protocols are complementary, with MCP handling model context and tools while A2A handles agent-to-agent orchestration.
How do I implement A2A protocol authentication for production agents?
Start with the official Python SDK or Agent Development Kit (ADK), which handles authentication flows automatically. For machine-to-machine communication, implement OAuth 2.0 client credentials flow and mutual TLS for high-security environments. Secure all authentication tokens using dedicated secret management systems and rotate credentials according to organizational policies. Validate authorization at every agent interaction point and design Agent Cards with minimal necessary permissions.
Is A2A protocol ready for production enterprise deployments in 2026?
A2A launched in April 2025, making it relatively new with limited production evidence. Microsoft's Semantic Kernel integration demonstrates technical viability, with a documented multi-agent travel planning use case on Azure App Service. However, most announced partnerships lack verified production deployments. Plan proof-of-concept validation before major commitments, start with non-critical workflows, and maintain architectural flexibility as the ecosystem matures.
How does A2A protocol handle long-running agent workflows?
A2A implements structured task lifecycles with defined states (pending, in-progress, completed, failed) and uses Server-Sent Events for real-time progress streaming. Agents submit tasks and receive task identifiers for tracking, subscribe to status updates rather than polling, and retrieve results when workflows complete asynchronously, supporting operations spanning hours or days.
Can Galileo monitor agents using the A2A protocol?
Standardized protocols like A2A enable unified visibility across multi-agent systems through defined communication standards. The protocol's architecture supports tracing agent decision paths through structured message logging, detecting failure patterns through standardized error handling and task lifecycle states, enforcing security guardrails through built-in authentication and authorization mechanisms, and maintaining audit trails through documented task states and transaction logs. This standardized approach enables observability across agents regardless of which vendor built each agent.
Your customer service agent needs to check inventory, your inventory agent must coordinate with suppliers, and those supplier agents operate on completely different platforms. Right now, each integration requires custom code, proprietary APIs, and weeks of engineering time.
Google's Agent2Agent (A2A) protocol addresses this fragmentation with a standardized communication layer that enables AI agents from different vendors and frameworks to discover, authenticate, and collaborate seamlessly.
TLDR:
A2A is an open-source protocol for secure agent-to-agent communication across platforms
Uses standard web technologies (JSON-RPC 2.0, HTTP/HTTPS, SSE) for straightforward integration
Different from MCP: A2A handles agent coordination; MCP connects agents to tools
Addresses vendor lock-in identified as a critical AI blind spot
Early adoption phase: Microsoft integrated; limited production deployments as of early 2025
Linux Foundation governance provides vendor-neutral community development
What Is Google's Agent2Agent Protocol?

Google's Agent2Agent (A2A) protocol is an open-source communication standard that enables autonomous AI agents to discover, authenticate, and interact with each other regardless of their underlying implementation or hosting platform.
Released in April 2025 under Apache-2.0 licensing and now governed by the Linux Foundation, A2A provides the interoperability layer that multi-agent systems require to operate across organizational and vendor boundaries.
A2A addresses a specific technical challenge: your agents built with different frameworks, deployed on different clouds, and operated by different organizations need to collaborate on complex workflows without requiring custom integration code for each connection.
A2A achieves this through standardized discovery mechanisms using Agent Cards, structured task management with defined lifecycle states, and enterprise-grade security including OAuth 2.0, API Keys, and mTLS support, all built on familiar web technologies (HTTP/HTTPS, JSON-RPC 2.0, Server-Sent Events) that your teams already understand.
Why enterprises need standardized agent interoperability

You face converging pressures that standardized protocols directly address. Vendor lock-in risks limit technical agility and weaken negotiating leverage. Integration complexity consumes 20-40% of engineering resources. Governance gaps in autonomous systems require comprehensive frameworks.
Industry analysts identify ecosystem lock-in as critical generative AI blind spots that CIOs must address to avoid project failures. While choosing a single vendor accelerates initial deployment, this creates dependency risks that constrain your technical options on pricing and service levels.
Organizations spend 20-40% of development time on integration maintenance. Without standardized protocols, integration complexity grows quadratically while engineering capacity remains linear.
Multi-agent systems increase organizational risk through multiple interacting autonomous agents, each making decisions that impact business outcomes and regulatory compliance. Comprehensive governance requirements include:
Identity and access management for agents operating across systems
Third-party risk management for agent interactions with external systems
Continuous monitoring with audit trails for accountability
Risk assessment frameworks adapted for autonomous decision-making
Without standardized protocols, implementing consistent AI guardrails across heterogeneous agent systems becomes exponentially complex.
Standardized agent communication protocols enable comprehensive observability across multi-agent workflows by providing unified visibility into agent interactions regardless of which vendor built each agent. When agents communicate through standardized protocols like A2A, monitoring becomes possible at the protocol level: tracking decision-making across workflows, identifying failure patterns, and maintaining audit trails required for compliance.
Core technical architecture and components
Understanding A2A's architecture reveals how it reduces integration friction while maintaining enterprise security standards. The protocol builds on technologies your teams already understand rather than introducing proprietary systems, making adoption more straightforward than custom agent-to-agent solutions that require specialized knowledge.
A2A builds on standards your teams already understand rather than introducing proprietary protocols. The architecture uses JSON-RPC 2.0 over HTTP/HTTPS for request-response patterns and Server-Sent Events (SSE) for real-time streaming, providing language-agnostic integration with standard web security through TLS.
Discovery mechanisms enable dynamic agent coordination
Agent Cards are JSON metadata files that function as machine-readable capability advertisements. Each agent hosts its Agent Card at the standardized well-known URI path /.well-known/agent.json, following RFC 8615 conventions. The card declares service endpoints, supported authentication schemes, skill descriptions with input/output modes, and specific task capabilities.
This standardized discovery mechanism allows any A2A client to programmatically discover what a remote agent can do without requiring vendor-specific knowledge. The cards support OAuth 2.0, API keys, OpenID Connect, and bearer tokens, giving you flexibility to match your organization's security policies.
Structured lifecycle tracking manages distributed workflows
A2A's task management system is specifically designed to handle long-running operations with defined lifecycle states. The protocol enables agents to track tasks through pending, in-progress, completed, and failed states, with Server-Sent Events (SSE) streaming real-time progress updates. This approach reduces network overhead while maintaining visibility into distributed workflows.
The protocol structures agent communication through Message Objects that support multiple content modalities. Message Parts can contain text, images, structured data, or other formats, allowing agents to exchange whatever data types their workflows require.
Artifact handling provides typed data exchange between agents. When one agent produces outputs that another agent needs (documents, images, executable code, or structured datasets), Artifacts provide the container format with metadata about content type, encoding, and semantics.
How A2A enables cross-vendor communication
The protocol achieves vendor-agnostic interoperability through five foundational design principles: embracing agentic capabilities for autonomous decision-making, building on existing standards rather than proprietary protocols, implementing security by default with enterprise-grade authentication, supporting long-running task lifecycles, and maintaining modality agnosticism for diverse content types.
Web standards foundation accelerates integration
A2A's foundation on established web standards (HTTP(S), JSON-RPC 2.0, and Server-Sent Events) directly reduces integration complexity that typically consumes 20-40% of development time in AI agent deployments.
By leveraging protocols that engineering teams already understand, the protocol reduces switching costs and enables language-agnostic integration through standardized request/response patterns.
The client-server architecture enables agents built with different frameworks to communicate without requiring knowledge of internal implementations. Microsoft has demonstrated this interoperability by integrating Semantic Kernel agents with the A2A protocol, enabling heterogeneous agent systems to coordinate with agents from different vendors and platforms operating alongside each other.
Enterprise security requires multiple authentication layers
Enterprise-grade security becomes essential when agents operated by different organizations communicate across trust boundaries. A2A incorporates multiple authentication mechanisms aligned with OpenAPI standards:
OAuth 2.0 for delegated authorization
Mutual TLS certificates for strong mutual authentication
JWT (JSON Web Tokens) for stateless authentication
API keys for simpler authentication scenarios
OpenID Connect for identity verification
Independent security analysis validates the protocol's Agent Card management security, authentication flows, and authorization enforcement mechanisms, though you should be aware of identified limitations in sensitive data handling that may require additional security enhancements beyond the base specification.
A2A protocol and Anthropic's MCP serve different purposes
Choosing the right protocol, or combination, depends on understanding which communication problems you're actually solving. A2A and MCP address fundamentally different architectural challenges in your agent infrastructure, and confusion between them leads to mismatched implementations.
Architecture models determine communication patterns
A2A implements a client-server model supporting Agent Cards for discovery, Task Management for structured lifecycles, Message-Based Collaboration for bidirectional agent communication, and Artifact Handling for typed data exchange. The architecture supports many-to-many agent relationships enabling mesh topologies where agents collaborate as peers.
MCP defines a client-server model where an AI application (MCP Host) maintains connections to tool servers providing context and capabilities. The key distinction: A2A enables peer-to-peer agent collaboration with bidirectional communication, while MCP implements a hub-and-spoke model where your AI application serves as the central orchestrator accessing tool servers and context providers.
Choosing between agent coordination and tool integration
Consider A2A when multiple autonomous agents need to collaborate across organizational boundaries. Picture this: your hiring pipeline with separate agents for screening, scheduling, and background checks requires agent-to-agent coordination through task delegation. Supply chain workflows where your agents must coordinate with external partner agents demand cross-organizational communication.
Choose MCP when one agent needs standardized access to multiple tools, data sources, or business systems. Suppose your customer support agent needs both capabilities. It uses MCP to access your knowledge base, ticket system, and customer database, standardizing how the agent connects to these tools. But when complex cases require escalation, your support agent uses A2A to coordinate with specialized agents handling refunds, technical issues, or billing disputes.
Implementation guidance for engineering teams
Your teams face several critical decisions when adopting A2A for production agent systems.
SDKs reduce integration risk and accelerate deployment
Begin with the official Python SDK rather than implementing the protocol from scratch. This decision cuts weeks of integration time while reducing the risk of protocol implementation errors that lead to production failures.
The SDK handles JSON-RPC formatting, HTTP transport management, and SSE streaming, allowing your developers to focus on agent logic rather than protocol plumbing. For teams building on Google Cloud, the Agent Development Kit provides higher-level abstractions managing connections and authentication automatically.
Study reference implementations before custom development. These samples demonstrate agent creation, task handling, client-server interactions, and complete workflow patterns, providing validated patterns your teams can adapt.
Orchestration patterns simplify complex workflows
Implement orchestrator agent patterns for complex workflows requiring coordination across multiple specialized agents. Orchestrator patterns reduce debugging complexity that typically consumes 20-40% of engineering time in distributed agent systems.
The orchestrator handles task decomposition into subtasks, delegates work to appropriate agents based on their declared capabilities in Agent Cards, manages state across the distributed workflow, and aggregates results from multiple agents.
When designing multi-agent systems with long-running tasks, implement proper error recovery and monitoring mechanisms to track task progress and agent interactions. A2A's task management system uses defined lifecycle states (pending, in-progress, completed, failed) to support extended workflows across distributed agents.
Production readiness and current adoption
As of early 2025, A2A protocol remains in early adoption phase with limited production deployment evidence. Understanding the maturity landscape helps your teams make informed architectural decisions.
Microsoft provides substantiated production-oriented implementation
Microsoft provides the most substantiated production-oriented implementation through Semantic Kernel integration. Microsoft's engineering team documented architecture details, provided code examples, and demonstrated multi-agent coordination through standardized communication. The travel planning reference shows a TravelManager agent coordinating with specialized sub-agents for flights, hotels, and activities.
Google announced partnerships with over 50 technology partners including Atlassian, Box, Intuit, MongoDB, PayPal, Salesforce, SAP, and ServiceNow, plus consulting firms like Accenture, BCG, Deloitte, and McKinsey. These partnerships represent commitments to support the protocol rather than verified production implementations.
Plan proof-of-concept validation before architectural commitments
Your teams should plan proof-of-concept validation before major architectural commitments. Test the protocol with representative workflows, validate security implementations meet your requirements, benchmark performance under realistic loads, and evaluate SDK maturity for your technology stack.
Think about phased adoption starting with non-critical workflows to gain operational experience, expanding to more critical systems as the ecosystem matures. Implement abstraction layers that accommodate protocol evolution or alternative standards.
Linux Foundation governance reduces long-term vendor risk
The transfer to Linux Foundation governance represents a fundamental shift from Google proprietary control to vendor-neutral community development under an open governance model. This governance structure reduces long-term vendor lock-in risk compared to single-vendor controlled specifications.
Active standards development continues across IEEE, W3C, and IETF working groups addressing agent communication in various contexts. The realistic future state involves multiple coexisting protocols rather than winner-takes-all outcomes. Design your architectures with abstraction layers accommodating protocol diversity as the ecosystem matures.
Agent interoperability shapes the future of enterprise AI
Standardized agent communication protocols transition from nice-to-have abstractions to strategic infrastructure requirements. Industry analysts project that by the end of 2026, 40% of enterprise applications will include task-specific AI agents, while simultaneously identifying ecosystem lock-in and interoperability as critical AI blind spots.
This convergence creates a strategic imperative for standardized protocols that prevent vendor lock-in while enabling sophisticated multi-agent workflows.
Galileo's platform provides the monitoring infrastructure that standardized protocols enable:
Agent Graph visualization: Map agent-to-agent communication flows across your entire ecosystem, identifying bottlenecks and failure patterns in multi-agent workflows regardless of which frameworks power each agent
Agent Protect with real-time guardrails: Block unsafe agent outputs before they reach production, enforcing compliance policies across heterogeneous agent systems communicating through A2A protocol
Insights Engine for multi-agent debugging: Trace decision paths through distributed workflows, pinpointing where agent handoffs fail and why task delegation breaks across vendor boundaries
Luna-2 evaluation models: Automatically assess agent output quality, hallucination rates, and task completion accuracy across agents using A2A for coordination
Protocol-agnostic monitoring: Track agent performance whether they communicate via A2A, MCP, or proprietary protocols—unified observability across your entire agent infrastructure
See how Galileo provides unified observability across multi-agent systems using A2A, MCP, and proprietary protocols—request a demo to visualize your agent ecosystem.
Frequently Asked Questions
What is the main difference between A2A and MCP protocols?
A2A enables peer-to-peer agent-to-agent coordination for multi-agent workflows through a client-server architecture where agents act as both clients and servers, while MCP implements a hub-and-spoke model connecting a single agent to multiple tools and data sources. A2A solves the horizontal problem of enabling autonomous agents to collaborate across different platforms and organizational boundaries; MCP solves the vertical problem of augmenting a single agent's capabilities through standardized tool integration. The two protocols are complementary, with MCP handling model context and tools while A2A handles agent-to-agent orchestration.
How do I implement A2A protocol authentication for production agents?
Start with the official Python SDK or Agent Development Kit (ADK), which handles authentication flows automatically. For machine-to-machine communication, implement OAuth 2.0 client credentials flow and mutual TLS for high-security environments. Secure all authentication tokens using dedicated secret management systems and rotate credentials according to organizational policies. Validate authorization at every agent interaction point and design Agent Cards with minimal necessary permissions.
Is A2A protocol ready for production enterprise deployments in 2026?
A2A launched in April 2025, making it relatively new with limited production evidence. Microsoft's Semantic Kernel integration demonstrates technical viability, with a documented multi-agent travel planning use case on Azure App Service. However, most announced partnerships lack verified production deployments. Plan proof-of-concept validation before major commitments, start with non-critical workflows, and maintain architectural flexibility as the ecosystem matures.
How does A2A protocol handle long-running agent workflows?
A2A implements structured task lifecycles with defined states (pending, in-progress, completed, failed) and uses Server-Sent Events for real-time progress streaming. Agents submit tasks and receive task identifiers for tracking, subscribe to status updates rather than polling, and retrieve results when workflows complete asynchronously, supporting operations spanning hours or days.
Can Galileo monitor agents using the A2A protocol?
Standardized protocols like A2A enable unified visibility across multi-agent systems through defined communication standards. The protocol's architecture supports tracing agent decision paths through structured message logging, detecting failure patterns through standardized error handling and task lifecycle states, enforcing security guardrails through built-in authentication and authorization mechanisms, and maintaining audit trails through documented task states and transaction logs. This standardized approach enables observability across agents regardless of which vendor built each agent.
Your customer service agent needs to check inventory, your inventory agent must coordinate with suppliers, and those supplier agents operate on completely different platforms. Right now, each integration requires custom code, proprietary APIs, and weeks of engineering time.
Google's Agent2Agent (A2A) protocol addresses this fragmentation with a standardized communication layer that enables AI agents from different vendors and frameworks to discover, authenticate, and collaborate seamlessly.
TLDR:
A2A is an open-source protocol for secure agent-to-agent communication across platforms
Uses standard web technologies (JSON-RPC 2.0, HTTP/HTTPS, SSE) for straightforward integration
Different from MCP: A2A handles agent coordination; MCP connects agents to tools
Addresses vendor lock-in identified as a critical AI blind spot
Early adoption phase: Microsoft integrated; limited production deployments as of early 2025
Linux Foundation governance provides vendor-neutral community development
What Is Google's Agent2Agent Protocol?

Google's Agent2Agent (A2A) protocol is an open-source communication standard that enables autonomous AI agents to discover, authenticate, and interact with each other regardless of their underlying implementation or hosting platform.
Released in April 2025 under Apache-2.0 licensing and now governed by the Linux Foundation, A2A provides the interoperability layer that multi-agent systems require to operate across organizational and vendor boundaries.
A2A addresses a specific technical challenge: your agents built with different frameworks, deployed on different clouds, and operated by different organizations need to collaborate on complex workflows without requiring custom integration code for each connection.
A2A achieves this through standardized discovery mechanisms using Agent Cards, structured task management with defined lifecycle states, and enterprise-grade security including OAuth 2.0, API Keys, and mTLS support, all built on familiar web technologies (HTTP/HTTPS, JSON-RPC 2.0, Server-Sent Events) that your teams already understand.
Why enterprises need standardized agent interoperability

You face converging pressures that standardized protocols directly address. Vendor lock-in risks limit technical agility and weaken negotiating leverage. Integration complexity consumes 20-40% of engineering resources. Governance gaps in autonomous systems require comprehensive frameworks.
Industry analysts identify ecosystem lock-in as critical generative AI blind spots that CIOs must address to avoid project failures. While choosing a single vendor accelerates initial deployment, this creates dependency risks that constrain your technical options on pricing and service levels.
Organizations spend 20-40% of development time on integration maintenance. Without standardized protocols, integration complexity grows quadratically while engineering capacity remains linear.
Multi-agent systems increase organizational risk through multiple interacting autonomous agents, each making decisions that impact business outcomes and regulatory compliance. Comprehensive governance requirements include:
Identity and access management for agents operating across systems
Third-party risk management for agent interactions with external systems
Continuous monitoring with audit trails for accountability
Risk assessment frameworks adapted for autonomous decision-making
Without standardized protocols, implementing consistent AI guardrails across heterogeneous agent systems becomes exponentially complex.
Standardized agent communication protocols enable comprehensive observability across multi-agent workflows by providing unified visibility into agent interactions regardless of which vendor built each agent. When agents communicate through standardized protocols like A2A, monitoring becomes possible at the protocol level: tracking decision-making across workflows, identifying failure patterns, and maintaining audit trails required for compliance.
Core technical architecture and components
Understanding A2A's architecture reveals how it reduces integration friction while maintaining enterprise security standards. The protocol builds on technologies your teams already understand rather than introducing proprietary systems, making adoption more straightforward than custom agent-to-agent solutions that require specialized knowledge.
A2A builds on standards your teams already understand rather than introducing proprietary protocols. The architecture uses JSON-RPC 2.0 over HTTP/HTTPS for request-response patterns and Server-Sent Events (SSE) for real-time streaming, providing language-agnostic integration with standard web security through TLS.
Discovery mechanisms enable dynamic agent coordination
Agent Cards are JSON metadata files that function as machine-readable capability advertisements. Each agent hosts its Agent Card at the standardized well-known URI path /.well-known/agent.json, following RFC 8615 conventions. The card declares service endpoints, supported authentication schemes, skill descriptions with input/output modes, and specific task capabilities.
This standardized discovery mechanism allows any A2A client to programmatically discover what a remote agent can do without requiring vendor-specific knowledge. The cards support OAuth 2.0, API keys, OpenID Connect, and bearer tokens, giving you flexibility to match your organization's security policies.
Structured lifecycle tracking manages distributed workflows
A2A's task management system is specifically designed to handle long-running operations with defined lifecycle states. The protocol enables agents to track tasks through pending, in-progress, completed, and failed states, with Server-Sent Events (SSE) streaming real-time progress updates. This approach reduces network overhead while maintaining visibility into distributed workflows.
The protocol structures agent communication through Message Objects that support multiple content modalities. Message Parts can contain text, images, structured data, or other formats, allowing agents to exchange whatever data types their workflows require.
Artifact handling provides typed data exchange between agents. When one agent produces outputs that another agent needs (documents, images, executable code, or structured datasets), Artifacts provide the container format with metadata about content type, encoding, and semantics.
How A2A enables cross-vendor communication
The protocol achieves vendor-agnostic interoperability through five foundational design principles: embracing agentic capabilities for autonomous decision-making, building on existing standards rather than proprietary protocols, implementing security by default with enterprise-grade authentication, supporting long-running task lifecycles, and maintaining modality agnosticism for diverse content types.
Web standards foundation accelerates integration
A2A's foundation on established web standards (HTTP(S), JSON-RPC 2.0, and Server-Sent Events) directly reduces integration complexity that typically consumes 20-40% of development time in AI agent deployments.
By leveraging protocols that engineering teams already understand, the protocol reduces switching costs and enables language-agnostic integration through standardized request/response patterns.
The client-server architecture enables agents built with different frameworks to communicate without requiring knowledge of internal implementations. Microsoft has demonstrated this interoperability by integrating Semantic Kernel agents with the A2A protocol, enabling heterogeneous agent systems to coordinate with agents from different vendors and platforms operating alongside each other.
Enterprise security requires multiple authentication layers
Enterprise-grade security becomes essential when agents operated by different organizations communicate across trust boundaries. A2A incorporates multiple authentication mechanisms aligned with OpenAPI standards:
OAuth 2.0 for delegated authorization
Mutual TLS certificates for strong mutual authentication
JWT (JSON Web Tokens) for stateless authentication
API keys for simpler authentication scenarios
OpenID Connect for identity verification
Independent security analysis validates the protocol's Agent Card management security, authentication flows, and authorization enforcement mechanisms, though you should be aware of identified limitations in sensitive data handling that may require additional security enhancements beyond the base specification.
A2A protocol and Anthropic's MCP serve different purposes
Choosing the right protocol, or combination, depends on understanding which communication problems you're actually solving. A2A and MCP address fundamentally different architectural challenges in your agent infrastructure, and confusion between them leads to mismatched implementations.
Architecture models determine communication patterns
A2A implements a client-server model supporting Agent Cards for discovery, Task Management for structured lifecycles, Message-Based Collaboration for bidirectional agent communication, and Artifact Handling for typed data exchange. The architecture supports many-to-many agent relationships enabling mesh topologies where agents collaborate as peers.
MCP defines a client-server model where an AI application (MCP Host) maintains connections to tool servers providing context and capabilities. The key distinction: A2A enables peer-to-peer agent collaboration with bidirectional communication, while MCP implements a hub-and-spoke model where your AI application serves as the central orchestrator accessing tool servers and context providers.
Choosing between agent coordination and tool integration
Consider A2A when multiple autonomous agents need to collaborate across organizational boundaries. Picture this: your hiring pipeline with separate agents for screening, scheduling, and background checks requires agent-to-agent coordination through task delegation. Supply chain workflows where your agents must coordinate with external partner agents demand cross-organizational communication.
Choose MCP when one agent needs standardized access to multiple tools, data sources, or business systems. Suppose your customer support agent needs both capabilities. It uses MCP to access your knowledge base, ticket system, and customer database, standardizing how the agent connects to these tools. But when complex cases require escalation, your support agent uses A2A to coordinate with specialized agents handling refunds, technical issues, or billing disputes.
Implementation guidance for engineering teams
Your teams face several critical decisions when adopting A2A for production agent systems.
SDKs reduce integration risk and accelerate deployment
Begin with the official Python SDK rather than implementing the protocol from scratch. This decision cuts weeks of integration time while reducing the risk of protocol implementation errors that lead to production failures.
The SDK handles JSON-RPC formatting, HTTP transport management, and SSE streaming, allowing your developers to focus on agent logic rather than protocol plumbing. For teams building on Google Cloud, the Agent Development Kit provides higher-level abstractions managing connections and authentication automatically.
Study reference implementations before custom development. These samples demonstrate agent creation, task handling, client-server interactions, and complete workflow patterns, providing validated patterns your teams can adapt.
Orchestration patterns simplify complex workflows
Implement orchestrator agent patterns for complex workflows requiring coordination across multiple specialized agents. Orchestrator patterns reduce debugging complexity that typically consumes 20-40% of engineering time in distributed agent systems.
The orchestrator handles task decomposition into subtasks, delegates work to appropriate agents based on their declared capabilities in Agent Cards, manages state across the distributed workflow, and aggregates results from multiple agents.
When designing multi-agent systems with long-running tasks, implement proper error recovery and monitoring mechanisms to track task progress and agent interactions. A2A's task management system uses defined lifecycle states (pending, in-progress, completed, failed) to support extended workflows across distributed agents.
Production readiness and current adoption
As of early 2025, A2A protocol remains in early adoption phase with limited production deployment evidence. Understanding the maturity landscape helps your teams make informed architectural decisions.
Microsoft provides substantiated production-oriented implementation
Microsoft provides the most substantiated production-oriented implementation through Semantic Kernel integration. Microsoft's engineering team documented architecture details, provided code examples, and demonstrated multi-agent coordination through standardized communication. The travel planning reference shows a TravelManager agent coordinating with specialized sub-agents for flights, hotels, and activities.
Google announced partnerships with over 50 technology partners including Atlassian, Box, Intuit, MongoDB, PayPal, Salesforce, SAP, and ServiceNow, plus consulting firms like Accenture, BCG, Deloitte, and McKinsey. These partnerships represent commitments to support the protocol rather than verified production implementations.
Plan proof-of-concept validation before architectural commitments
Your teams should plan proof-of-concept validation before major architectural commitments. Test the protocol with representative workflows, validate security implementations meet your requirements, benchmark performance under realistic loads, and evaluate SDK maturity for your technology stack.
Think about phased adoption starting with non-critical workflows to gain operational experience, expanding to more critical systems as the ecosystem matures. Implement abstraction layers that accommodate protocol evolution or alternative standards.
Linux Foundation governance reduces long-term vendor risk
The transfer to Linux Foundation governance represents a fundamental shift from Google proprietary control to vendor-neutral community development under an open governance model. This governance structure reduces long-term vendor lock-in risk compared to single-vendor controlled specifications.
Active standards development continues across IEEE, W3C, and IETF working groups addressing agent communication in various contexts. The realistic future state involves multiple coexisting protocols rather than winner-takes-all outcomes. Design your architectures with abstraction layers accommodating protocol diversity as the ecosystem matures.
Agent interoperability shapes the future of enterprise AI
Standardized agent communication protocols transition from nice-to-have abstractions to strategic infrastructure requirements. Industry analysts project that by the end of 2026, 40% of enterprise applications will include task-specific AI agents, while simultaneously identifying ecosystem lock-in and interoperability as critical AI blind spots.
This convergence creates a strategic imperative for standardized protocols that prevent vendor lock-in while enabling sophisticated multi-agent workflows.
Galileo's platform provides the monitoring infrastructure that standardized protocols enable:
Agent Graph visualization: Map agent-to-agent communication flows across your entire ecosystem, identifying bottlenecks and failure patterns in multi-agent workflows regardless of which frameworks power each agent
Agent Protect with real-time guardrails: Block unsafe agent outputs before they reach production, enforcing compliance policies across heterogeneous agent systems communicating through A2A protocol
Insights Engine for multi-agent debugging: Trace decision paths through distributed workflows, pinpointing where agent handoffs fail and why task delegation breaks across vendor boundaries
Luna-2 evaluation models: Automatically assess agent output quality, hallucination rates, and task completion accuracy across agents using A2A for coordination
Protocol-agnostic monitoring: Track agent performance whether they communicate via A2A, MCP, or proprietary protocols—unified observability across your entire agent infrastructure
See how Galileo provides unified observability across multi-agent systems using A2A, MCP, and proprietary protocols—request a demo to visualize your agent ecosystem.
Frequently Asked Questions
What is the main difference between A2A and MCP protocols?
A2A enables peer-to-peer agent-to-agent coordination for multi-agent workflows through a client-server architecture where agents act as both clients and servers, while MCP implements a hub-and-spoke model connecting a single agent to multiple tools and data sources. A2A solves the horizontal problem of enabling autonomous agents to collaborate across different platforms and organizational boundaries; MCP solves the vertical problem of augmenting a single agent's capabilities through standardized tool integration. The two protocols are complementary, with MCP handling model context and tools while A2A handles agent-to-agent orchestration.
How do I implement A2A protocol authentication for production agents?
Start with the official Python SDK or Agent Development Kit (ADK), which handles authentication flows automatically. For machine-to-machine communication, implement OAuth 2.0 client credentials flow and mutual TLS for high-security environments. Secure all authentication tokens using dedicated secret management systems and rotate credentials according to organizational policies. Validate authorization at every agent interaction point and design Agent Cards with minimal necessary permissions.
Is A2A protocol ready for production enterprise deployments in 2026?
A2A launched in April 2025, making it relatively new with limited production evidence. Microsoft's Semantic Kernel integration demonstrates technical viability, with a documented multi-agent travel planning use case on Azure App Service. However, most announced partnerships lack verified production deployments. Plan proof-of-concept validation before major commitments, start with non-critical workflows, and maintain architectural flexibility as the ecosystem matures.
How does A2A protocol handle long-running agent workflows?
A2A implements structured task lifecycles with defined states (pending, in-progress, completed, failed) and uses Server-Sent Events for real-time progress streaming. Agents submit tasks and receive task identifiers for tracking, subscribe to status updates rather than polling, and retrieve results when workflows complete asynchronously, supporting operations spanning hours or days.
Can Galileo monitor agents using the A2A protocol?
Standardized protocols like A2A enable unified visibility across multi-agent systems through defined communication standards. The protocol's architecture supports tracing agent decision paths through structured message logging, detecting failure patterns through standardized error handling and task lifecycle states, enforcing security guardrails through built-in authentication and authorization mechanisms, and maintaining audit trails through documented task states and transaction logs. This standardized approach enables observability across agents regardless of which vendor built each agent.


Jackson Wells